[ad_1]

Android malware developers are stepping up their billing fraud activity with applications that disable Wi-Fi connections, surreptitiously subscribe users to pricey wireless services, and intercept textual content messages, all in a bid to collect hefty expenses from unsuspecting end users, Microsoft stated on Friday.
This menace class has been a reality of existence on the Android platform for years, as exemplified by a loved ones of malware identified as Joker, which has contaminated thousands and thousands of phones given that 2016. In spite of recognition of the challenge, very little attention has been paid to the strategies that these “toll fraud” malware makes use of. Enter Microsoft, which has posted a technological deep dive on the difficulty.
The billing mechanism abused in this form of fraud is WAP, short for wi-fi application protocol, which supplies a usually means of accessing data about a cellular community. Mobile phone consumers can subscribe to this sort of providers by browsing a service provider’s world-wide-web web site when their equipment are connected to cellular assistance, then clicking a button. In some cases, the carrier will answer by texting a one particular-time password (OTP) to the phone and demanding the user to ship it back in order to validate the subscription request. The approach seems to be like this:
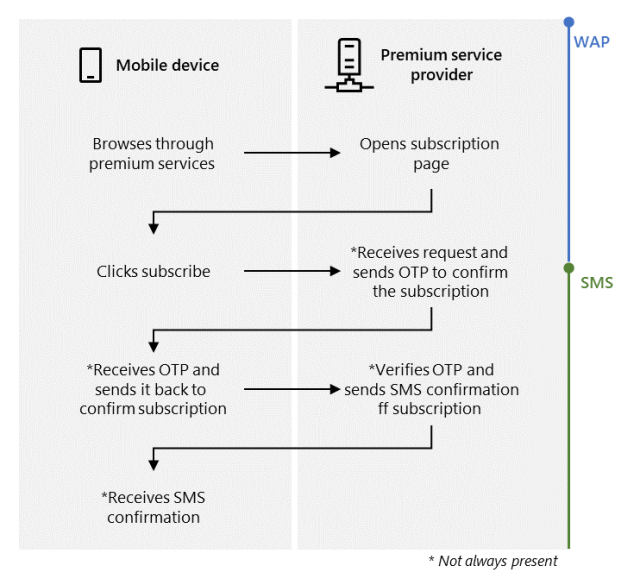
Microsoft
The intention of the malicious applications is to subscribe contaminated phones to these WAP solutions automatically, devoid of the detect or consent of the owner. Microsoft claimed that destructive Android apps its scientists have analyzed obtain this target by subsequent these actions:
- Disable the Wi-Fi connection or wait for the consumer to switch to a cell network
- Silently navigate to the subscription page
- Auto-simply click the membership button
- Intercept the OTP (if applicable)
- Send the OTP to the provider service provider (if applicable)
- Terminate the SMS notifications (if applicable)
Malware builders have several strategies to drive a cellphone to use a mobile link even when it is connected to Wi-Fi. On units managing Android 9 or earlier, the builders can invoke the setWifiEnabled method of the WifiManager course. For versions 10 and over, developers can use the requestNetwork function of the ConnectivityManager class. Inevitably, phones will load facts solely in excess of the cellular community, as shown in this picture:
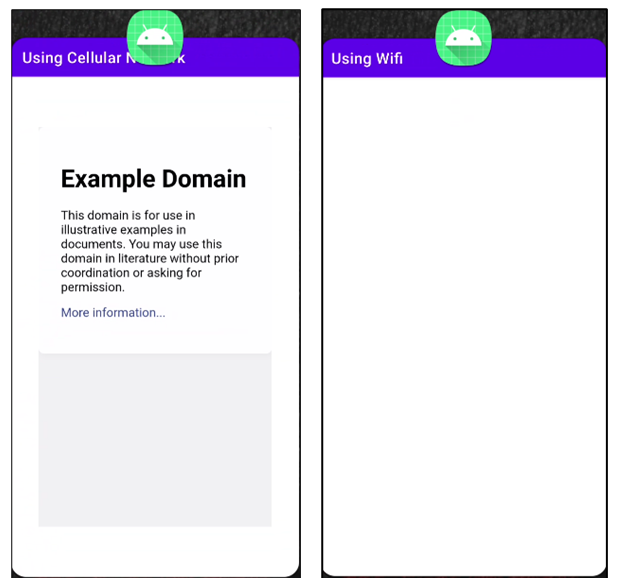
Microsoft
When a cell phone utilizes the cellular network for data transmission, the destructive app surreptitiously opens a browser in the history, navigates to the WAP subscription site, and clicks a subscribe button. Confirming the membership can be tough mainly because confirmation prompts can occur by SMS, HTTP, or USSD protocols. Microsoft lays out certain methods that malware developers can use to bypass each style of confirmation. The Microsoft submit then goes on to reveal how the malware suppresses periodic messages that the membership service may well deliver the person to remind them of their subscription.
“By subscribing users to high quality solutions, this malware can direct to victims acquiring important cellular invoice charges,” Microsoft researchers wrote. “Affected gadgets also have elevated threat due to the fact this risk manages to evade detection and can achieve a large selection of installations just before a one variant receives eradicated.”
Google actively bars apps from its Enjoy industry when it detects indications of fraud or malice, or when it gets experiences of destructive applications from 3rd events. Though Google generally does not clear away malicious apps until finally soon after they have contaminated millions of consumers, applications downloaded from Enjoy are typically regarded as far more honest than applications from third-celebration marketplaces.
[ad_2]
Source hyperlink


